Deobfuscating .Net executable
All the .Net malware that I have analyzed they were obfuscated. The first step to analyze a .Net malware it’s to deobfuscate it. The best tool that i know for this purpose it’s de4dot:
de4dot.exe <path to .Net executable>
It will leave other executable in the same directory of the target executable with the additional extension .clean.
Decompiling .Net executable
In the case of .Net malware it’s much easier to decompile the executable with specific tools than reading MSIL code with a disassembler like IDA.
IlSpy
IlSpy it’s a .Net decompiler that works fine.
JetBrains dotPeek
Other good decompiler. It’s slower, but you can generate a visual studio project with the decompiled sources.
Debugging .Net executables
Dotnet IL Editor
Dile it is an editor and MSIL debugger for .Net. Working with it I found it usually crashes suddenly. Anyway there are not too much debuggers and it works well.
Analyzing SamSam ransomware
After deobfuscating and decompiling it with IlSpy we can start to explore the code easily.
Encrypted strings
The most important strings used by the ransomware are encrypted with AES and key SALT.
They are decrypted with the key “SALT” and the algorithm in the function myff11:
With Jetbrains dotPeek it is easy to create a visual studio project and compile the code of the ransom. In this way we can leave it to decrypt the strings and see easily the decrypted content of these strings. Here you can find a compilable visual studio project:
Malware-Analysis/tree/master/ransomware_samsam/decompiled_code
(I have renamed the original Main function to MainOriginal and i added a empty Main. If you want to debug the full behaviour of the ransom you should call MainOriginal).
We compile the code and we can debug the code that we are interested on, and we can see the content of decrypted variables. For example here we can see the list of extensions that malware will encrypt:
Interesting info in the encrypted strings
Extensions list
.vb,.asmx,.config,.3dm,.3ds,.3fr,.3g2,.3gp,.3pr,.7z,.ab4,.accdb,.accde,.accdr,.accdt,
.ach,.acr,.act,.adb,.ads,.agdl,.ai,.ait,.al,.apj,.arw,.asf,.asm,.asp,.aspx,.asx,.avi,.awg,
.back,.backup,.backupdb,.bak,.lua,.m,.m4v,.max,.mdb,.mdc,.mdf,.mef,.mfw,.mmw,
.moneywell,.mos,.mov,.mp3,.mp4,.mpg,.mrw,.msg,.myd,.nd,.ndd,.nef,.nk2,.nop,
.nrw,.ns2,.ns3,.ns4,.nsd,.nsf,.nsg,.nsh,.nwb,.nx2,.nxl,.nyf,.tif,.tlg,.txt,.vob,.wallet,
.war,.wav,.wb2,.wmv,.wpd,.wps,.x11,.x3f,.xis,.xla,.xlam,.xlk,.xlm,.xlr,.xls,.xlsb,
.xlsm,.xlsx,.xlt,.xltm,.xltx,.xlw,.xml,.ycbcra,.yuv,.zip,.sqlite,.sqlite3,.sqlitedb,.sr2,
.srf,.srt,.srw,.st4,.st5,.st6,.st7,.st8,.std,.sti,.stw,.stx,.svg,.swf,.sxc,.sxd,.sxg,.sxi,.sxm,
.sxw,.tex,.tga,.thm,.tib,.py,.qba,.qbb,.qbm,.qbr,.qbw,.qbx,.qby,.r3d,.raf,.rar,.rat,
.raw,.rdb,.rm,.rtf,.rw2,.rwl,.rwz,.s3db,.sas7bdat,.say,.sd0,.sda,.sdf,.sldm,.sldx,
.sql,.pdd,.pdf,.pef,.pem,.pfx,.php,.php5,.phtml,.pl,.plc,.png,.pot,.potm,.potx,
.ppam,.pps,.ppsm,.ppsx,.ppt,.pptm,.pptx,.prf,.ps,.psafe3,.psd,.pspimage,.pst,
.ptx,.oab,.obj,.odb,.odc,.odf,.odg,.odm,.odp,.ods,.odt,.oil,.orf,.ost,.otg,.oth,.otp,
.ots,.ott,.p12,.p7b,.p7c,.pab,.pages,.pas,.pat,.pbl,.pcd,.pct,.pdb,.gray,.grey,.gry,
.h,.hbk,.hpp,.htm,.html,.ibank,.ibd,.ibz,.idx,.iif,.iiq,.incpas,.indd,.jar,.java,.jpe,
.jpeg,.jpg,.jsp,.kbx,.kc2,.kdbx,.kdc,.key,.kpdx,.doc,.docm,.docx,.dot,.dotm,.dotx,
.drf,.drw,.dtd,.dwg,.dxb,.dxf,.dxg,.eml,.eps,.erbsql,.erf,.exf,.fdb,.ffd,.fff,.fh,.fhd,
.fla,.flac,.flv,.fmb,.fpx,.fxg,.cpp,.cr2,.craw,.crt,.crw,.cs,.csh,.csl,.csv,.dac,.bank,
.bay,.bdb,.bgt,.bik,.bkf,.bkp,.blend,.bpw,.c,.cdf,.cdr,.cdr3,.cdr4,.cdr5,.cdr6,
.cdrw,.cdx,.ce1,.ce2,.cer,.cfp,.cgm,.cib,.class,.cls,.cmt,.cpi,.ddoc,.ddrw,.dds,.der,.des,
.design,.dgc,.djvu,.dng,.db,.db-journal,.db3,.dcr,.dcs,.ddd,.dbf,.dbx,.dc2,.pbl, .sql,.mdf
Rescue html message
Here you can find the content of the html message:
Malware-Analysis/blob/master/ransomware_samsam/READ-FOR-DECCCC-FILESSS.html
File encryption
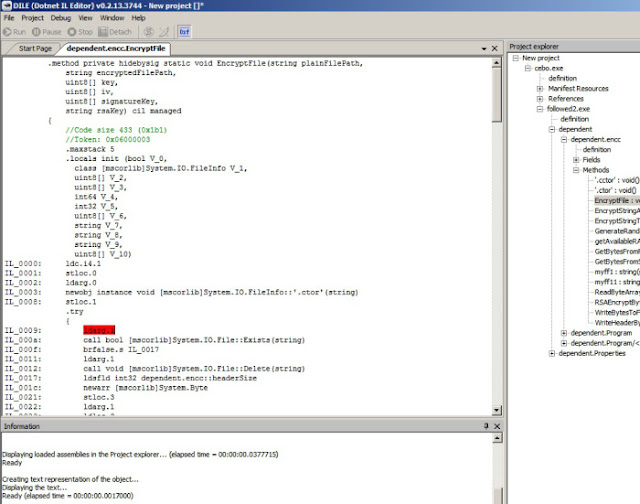
The encryption of files is done with the function encc.myff1 and encc.EncryptFile.
It will write the encrypted contents to a file with <originalname> + “.breeding123” extension:
After encrypting a file, it will delete the original file, leaving the encrypted one. However i can’t see a point of the malware calling vssadmin or bcdedit, or cleaning removed file sectors. So it could be possible to recover file contents or a part of them. But i have not tested it.
It creates a random key for encrypting file content with AES. After that it encrypts the AES key with a public RSA that the malware carries with itself. Finally, it writes the encrypted content with a header containing the encrypted AES key to the .breeding123 file.
EncryptFile:









No comments:
Post a Comment